Remote working and BYOD (Bring Your Own Device) approaches are now the norm throughout society. This means employees using their personal devices to work and access corporate data.
Whilst an excellent display of resourcefulness and resilience in current tough times; for IT managers operating with outdated IT solutions, this could be a cause for major concern. How could they keep company data safe with various device types and software versions being used? A one-size-fits-all approach to Device Management was no longer possible.
Luckily, this is a worry that Google Workspace (Formerly known as G Suite) users need not have. Here at Cobry, we can aid you in implementing Google's security features that ensure your Google Workspace data is completely safe - even when operating with a BYOD strategy. Let’s take a look at them now.
Google Endpoint Management for BYOD Devices
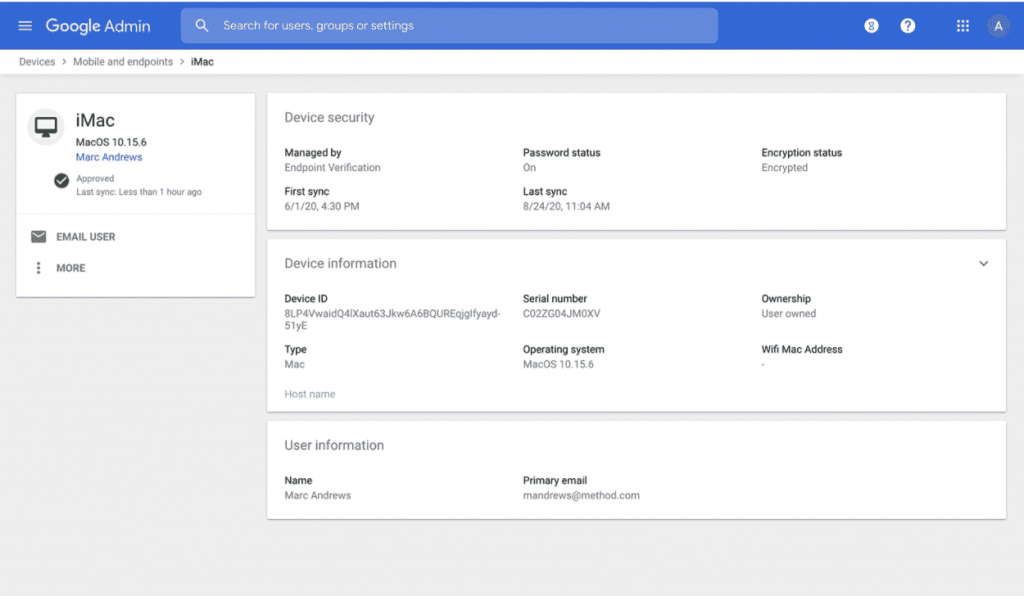
Google Endpoint Management ensures a secure BYOD approach by applying a base level of security to every device (Corporate and BYOD) that accesses Google Workspace (Formerly known as G Suite) data. IT managers can support a variety of device models (mobile and desktop) by requiring minimum software versions and refusing the use of jailbroken or rooted devices.
When a device logs into a Google Workspace account through any browser on a Windows, Mac, Chrome or Linux device, it is automatically enrolled with Endpoint Management. This gives IT admins access to valuable information such as the device type, operating system, and its first and last sync to the admin console.
This data aids admins in making more informed decisions around Device Management and security. Moreover, it provides a clear understanding of all of the devices that are accessing corporate information. By enrolling in Endpoint Management, Cobry can aid you in taking important remedial action if a device has been lost, stolen or compromised. For example, we can remotely log users out from devices and wipe compromised Google accounts.
So, no matter the device type and no matter the operating system; Endpoint Management gives you the information needed to effectively manage a BYOD approach.
Device Management for BYOD Mobile Devices
If use of mobile devices is part of your organisation's BYOD approach, Google Workspace still has you covered. Google offers two solutions for mobile Device Management - Basic and Advanced.
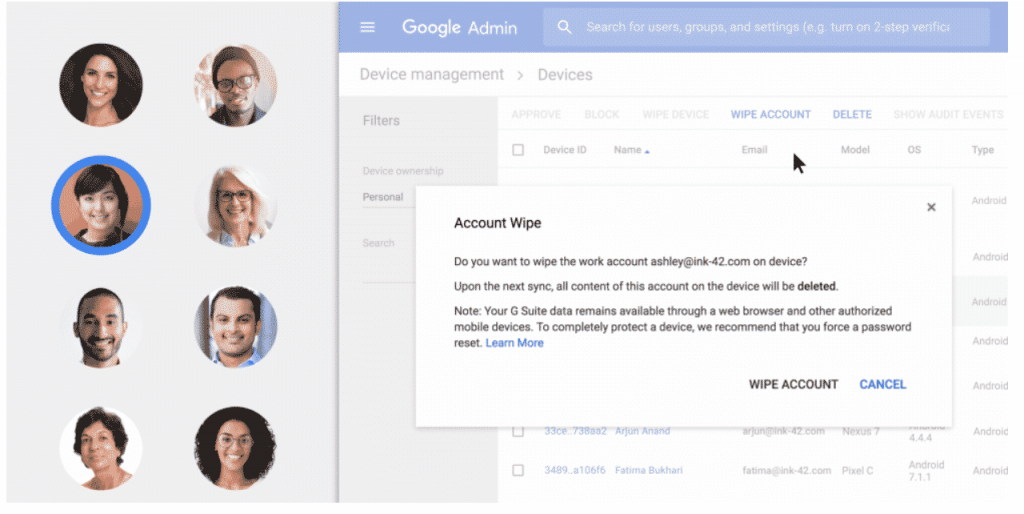
Basic Mobile Device Management ensures BYOD mobile devices are secured with baseline security features. With this feature, it is possible to:
- enforce passcodes
- Remotely wipe Google data
- Receive device inventory
- Remotely force install applications on android devices
Using Advanced Mobile Device Management, it is possible for:
- IT admins to apply additional controls over BYOD devices
- Android users to use Android Profiles which keep their work and private data separate on the same device
Context-aware Access on BYOD Devices
Context-aware access uses information such as user identity, location, device security status and IP address to grant (or deny) access to Google Workspace services. This means that Google Workspace services - and data that may be stored there - are protected against unauthorised access without the need for a VPN.
Cobry can help you make the most out of Context-aware Access by administering different levels of access depending on user attributes. For example, on BYOD devices, controls can be put in place to increase security levels such as encryption and password requirements to access various Google Workspace services.
Therefore, through knowledge of these attributes, you can give access to the right BYOD devices and reject access requests from unwanted devices.
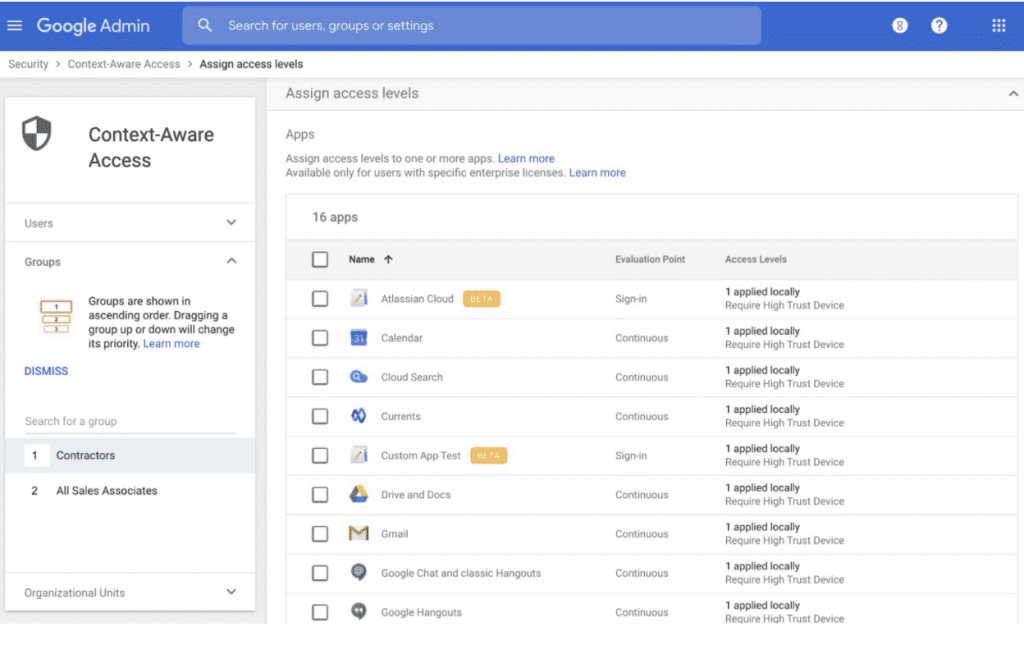
App access control on BYOD Devices
App Access Control allows IT admins to protect corporate and BYOD devices from malicious app attacks. IT admins have full control over which third party apps are allowed to access Google Workspace data. This means they can choose to trust, limit or block access for particular apps. So, even when implementing a BYOD strategy, rest assured that important company data will remain in safe - and the correct - hands.
BYOD 2-Factor Authentication
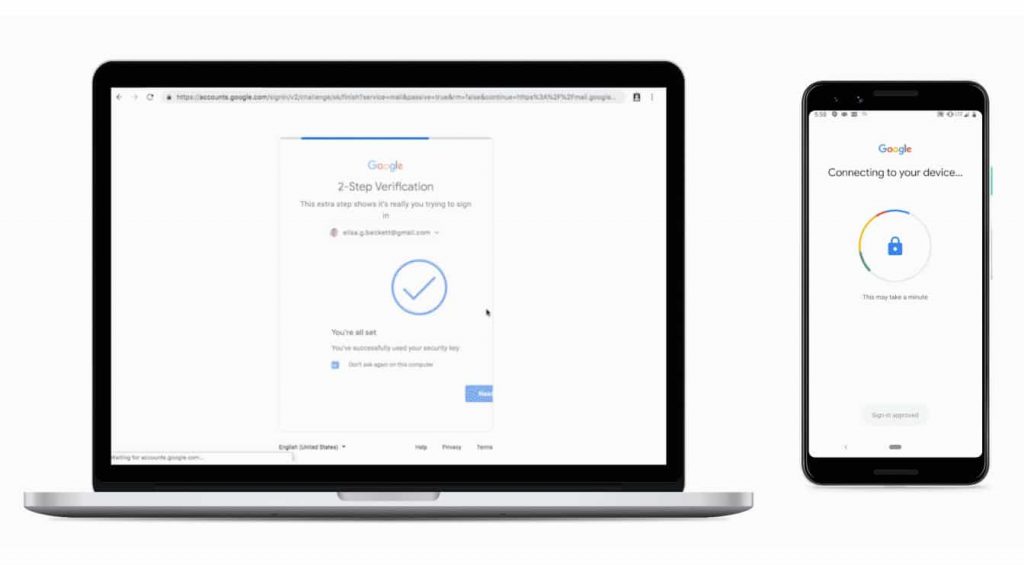
2-Factor Authentication (2FA) ensures a secure BYOD strategy by requiring additional proof of identity before accessing a Google Workspace account. Step 1 includes the provision of user-sensitive information such as a password. Step 2 requires that the user use something they have to gain access. For example, an access code delivered to a different device via text message, or a third party app such as Google Authenticator. This ensures that even if a BYOD has been compromised, Google Workspace data will remain secured.
Google also offers its Advanced Protection Program to those most at risk of being targeted by online attackers. The Advanced Protection Program goes beyond 2FA by requiring the use of a physical Security Key when logging on from a new device. This means that attackers will be unable to access the Google Workspace account, even if a password has been compromised.
When being used on Google Chrome, files are automatically scanned and users are warned of potentially harmful downloads. Additionally, it blocks access from untrusted apps and provides enhanced scanning for email threats.
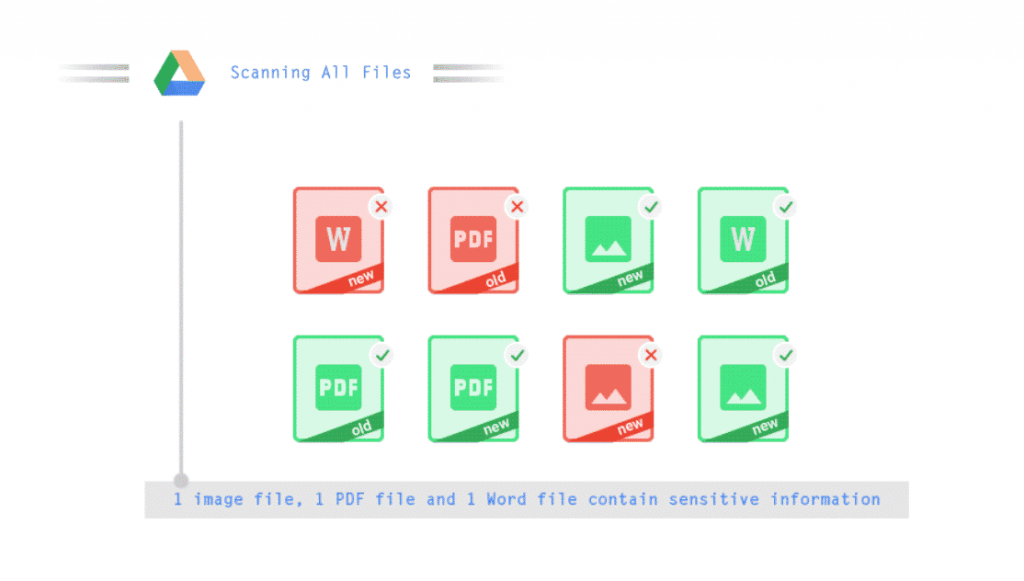
Data Loss Prevention
Data loss prevention (DLP) helps to protect information held in Google Drive, Docs, Sheets, Slides and Gmail from being lost, deleted or misused. Cobry can aid you in setting policies that specify which types of data are sensitive and how they should be protected. Therefore, you can be certain that your organisations important data will always be safe.
We can also enable Data Exfiltration Protection (DXP) on iOS devices to prohibit copying and pasting Google Workspace data to other accounts. It restricts the ability to drag and drop files from specific apps within users’ Google Workspace accounts. Meanwhile, on Android devices, it is possible to prevent data sharing between profiles by using Google Endpoint Management.
Retention and eDiscovery with Vault
Finally, Vault enables corporate data accessed by BYOD or corporate owned devices to support the organisation's retention and eDiscovery needs. This means that you can be assured data is always accessible to Vault, even on BYOD devices.
Thanks to these great features, Google Workspace users need not fret over BYOD security. No matter the device type or system, whether is corporate-owned or BYOD; enabling these features will ensure your organisations important data is always secured. Just what we all needed to hear as we embark on the coming months of remote working!
Want to know more about how Cobry can help you keep your organisation safe? Book a discovery call or drop us a message to chat to us.







